Technical support for software users is crucial for ensuring user satisfaction and successful software adoption. This involves understanding diverse user needs, identifying common software issues, and implementing effective support strategies across multiple channels. From proactive problem prevention to responsive troubleshooting, efficient technical support is paramount for a positive user experience and the overall success of any software application.
This exploration delves into the multifaceted aspects of providing exceptional technical support, encompassing user profiling, troubleshooting methodologies, knowledge base development, remote assistance techniques, training material creation, and efficient ticket management. We will also examine proactive support strategies, the importance of measuring support effectiveness, and crucial accessibility and security considerations.
Common Software Issues
Software malfunctions are a frustratingly common occurrence, impacting productivity and user experience. Understanding the root causes of these issues is crucial for effective troubleshooting and prevention. This section Artikels five of the most frequently reported problems, their underlying causes, and potential solutions.
Software Crashes and Freezes
Software crashes and freezes are characterized by the unexpected termination of a program or the complete unresponsiveness of the system. This can manifest as the program abruptly closing, the screen freezing, or the system becoming unresponsive to input. Causes include insufficient system resources (RAM, CPU), corrupted system files, driver conflicts, software bugs, or malware infections. Solutions range from restarting the computer, updating drivers and software, running a malware scan, increasing RAM, to reinstalling the problematic software or even the operating system in severe cases. For instance, a game might crash due to insufficient video RAM, while a system freeze could result from a conflict between two outdated drivers.
Slow Performance
Slow performance is a broad term encompassing sluggish response times, extended loading periods, and general system lag. This can stem from a variety of sources, including insufficient RAM, a fragmented hard drive, a large number of background processes, malware, outdated software, or a lack of hard drive space. Solutions involve upgrading RAM, defragmenting or upgrading to an SSD, closing unnecessary applications, running a malware scan, updating software, and deleting unnecessary files. For example, a computer with only 4GB of RAM might struggle to run multiple demanding applications simultaneously, leading to significant slowdowns.
Application Errors, Technical support for software users
Application errors manifest as error messages, often accompanied by codes, indicating specific problems within the software. These errors can result from bugs in the software’s code, corrupted files, incompatible hardware or software, or incorrect configuration settings. Troubleshooting involves checking for updates, verifying file integrity, reinstalling the application, adjusting settings, or checking for hardware compatibility. A common example is an error message indicating a missing DLL file, suggesting a corrupted installation or missing dependency.
Internet Connectivity Issues
Problems connecting to the internet can prevent access to online services and applications. These issues may be caused by network configuration problems, router malfunctions, internet service provider (ISP) outages, firewall restrictions, or malware interference. Solutions include checking network cables, restarting the router and modem, contacting the ISP, checking firewall settings, and running a malware scan. For instance, an incorrect IP address configuration can prevent a device from accessing the internet.
Data Loss or Corruption
Data loss or corruption refers to the inaccessibility or alteration of important files and data. Causes range from accidental deletion, hardware failure, software malfunctions, power outages, and malware attacks. Prevention is key here, employing regular backups, using reliable storage media, and maintaining updated antivirus software. Recovery methods vary depending on the cause, from using data recovery software to restoring from backups. A hard drive crash, for example, could lead to significant data loss unless regular backups were in place.
Knowledge Base Development
A well-structured knowledge base is crucial for effective software support. It empowers users to resolve common issues independently, reducing the burden on support teams and improving overall user satisfaction. A well-organized knowledge base also provides a centralized repository of information, ensuring consistency and accuracy across all support channels.
This section details the creation of a knowledge base article addressing a specific software error, along with a frequently asked questions (FAQ) section and a hierarchical structure for improved navigation.
Troubleshooting the “Error Code 1234”
Error Code 1234 typically indicates a problem with the software’s connection to the database server. This error message usually appears when the software is unable to establish a connection, or the connection is interrupted unexpectedly. Several factors can contribute to this issue, including network connectivity problems, database server outages, or incorrect configuration settings within the software.
Steps to Resolve Error Code 1234:
Effective technical support is crucial for all software users, ensuring smooth operation and minimizing disruptions. This is especially vital for complex systems like HR and payroll software , where accurate data management is paramount. Therefore, robust support channels are key to user satisfaction and efficient workflow processes.
- Verify Network Connectivity: Ensure your computer is connected to the internet and that the network connection is stable. Try accessing other online resources to rule out network issues. A simple ping test to the database server’s IP address can confirm connectivity.
- Check Database Server Status: Confirm that the database server is operational. If you have access to server monitoring tools, check for any reported outages or service disruptions. If not, contact your system administrator.
- Examine Software Configuration: Verify that the software’s database connection settings are correct. This typically involves checking the server address, port number, database name, username, and password. Ensure that these settings match the information provided by your system administrator.
- Restart the Software and Computer: A simple restart can often resolve temporary glitches that might be causing the connection problem. Restart the software first, and if the error persists, restart your computer.
- Reinstall the Software (Last Resort): If the above steps fail, reinstalling the software might be necessary. Before doing so, back up any important data to avoid data loss. Ensure you download the software from a trusted source.
Frequently Asked Questions (FAQ)
This section addresses common questions related to Error Code 1234 and general software usage.
Effective technical support for software users often involves addressing a wide range of issues. A significant aspect, especially for cloud-based applications, is understanding the potential vulnerabilities. For instance, a user might experience connectivity problems stemming from issues detailed in this insightful article on Security challenges in the cloud. Therefore, comprehensive support must encompass both software functionality and the security landscape impacting user experience.
- What does Error Code 1234 mean? Error Code 1234 indicates a failure to connect to the database server. This is often caused by network issues, server problems, or incorrect software configuration.
- Why am I getting this error message? The error can occur due to various reasons, including network connectivity problems, database server outages, or incorrect database connection settings within the software.
- How can I prevent Error Code 1234 from occurring? Regularly check your network connection and database server status. Ensure that your software’s database connection settings are accurate and up-to-date. Consider setting up automated alerts for database server outages.
- What should I do if I continue to receive this error after trying the troubleshooting steps? Contact your system administrator or technical support for further assistance. Provide them with details of the steps you have already taken and any error messages you are receiving.
Knowledge Base Structure
The knowledge base will be organized hierarchically. The top level will categorize issues by software module (e.g., Data Entry, Reporting, Administration). Each module will have sub-categories based on the type of issue (e.g., Connection Errors, Data Errors, Performance Issues). Within each sub-category, specific error codes and troubleshooting steps will be detailed. A search function will allow users to quickly find relevant articles.
Training Materials Creation
Effective training materials are crucial for user adoption and satisfaction. Well-designed tutorials and interactive modules can significantly reduce the learning curve and improve user proficiency with the software. This section details the creation of various training resources to support our users.
Creating comprehensive training materials involves a multi-faceted approach, encompassing visual aids, step-by-step instructions, and interactive elements. The goal is to provide users with a clear and engaging learning experience, enabling them to quickly master the software’s functionalities.
Short Tutorial Video Explaining a Key Software Feature
This video tutorial will focus on explaining the software’s automated report generation feature. The video will begin with an introduction to the feature’s purpose and benefits. Then, a screen recording will demonstrate the step-by-step process of accessing the feature, configuring the report parameters (date range, data filters, etc.), and finally generating and exporting the report in various formats (PDF, CSV, Excel). The video will conclude with a brief summary and pointers to further resources. Visual cues, such as highlighted buttons and on-screen text annotations, will guide the viewer through the process. The video’s audio narration will be clear, concise, and easy to understand.
Step-by-Step Instructions for Completing a Complex Task
A series of step-by-step instructions will be created to guide users through the process of integrating the software with a third-party CRM system. This complex task involves several interconnected steps, including API key generation, configuration settings adjustments, data mapping, and testing the integration. Each step will be clearly Artikeld, with screenshots illustrating each stage of the process. The instructions will use simple, unambiguous language and avoid technical jargon where possible. Error messages and troubleshooting tips will be included to assist users in resolving common issues encountered during the integration process. A checklist at the end will allow users to verify the completion of each step.
Interactive Training Modules to Enhance User Understanding
Interactive training modules will be developed using a scenario-based approach. For example, one module might simulate a typical workflow within the software, presenting users with various scenarios and requiring them to select the appropriate actions. Feedback will be provided after each selection, guiding the user toward the correct solution and explaining the rationale behind it. Another module could use quizzes and knowledge checks to assess user understanding of key concepts. These modules will use a visually appealing design, incorporating graphics and animations to keep users engaged. Progress tracking will be implemented to monitor user completion and identify areas where additional support may be needed. The interactive nature of these modules promotes active learning and reinforces user comprehension.
Support Ticket Management
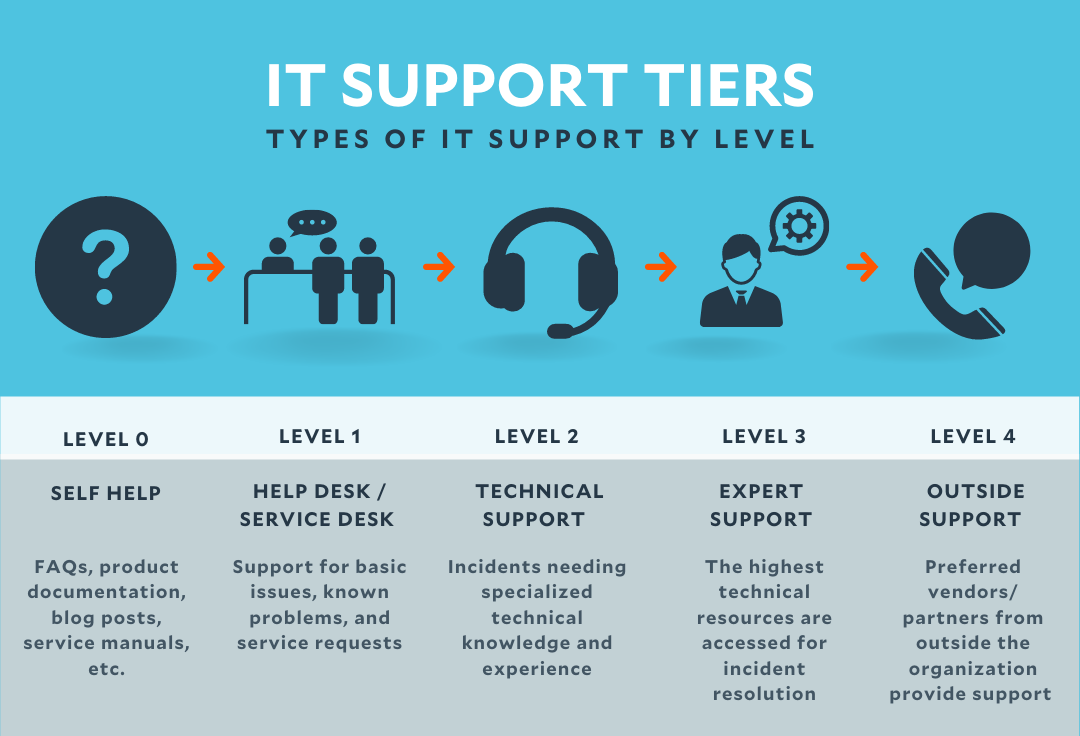
Effective support ticket management is crucial for providing timely and efficient assistance to software users, maintaining customer satisfaction, and improving overall operational efficiency. A well-structured system ensures that issues are addressed promptly and appropriately, minimizing downtime and maximizing user productivity.
A robust support ticket management system involves several key components working together to streamline the process from initial submission to final resolution. This includes clear prioritization, efficient escalation procedures, and meticulous tracking of key metrics.
Ticket Prioritization
Prioritizing support tickets ensures that critical issues receive immediate attention while less urgent ones are addressed in a timely manner. A common approach uses a tiered system, often based on the impact on the user and the urgency of resolution. For example, a critical issue might be a complete system outage affecting multiple users, while a low-priority issue could be a minor cosmetic bug affecting only a single user. Tickets can be assigned priority levels (e.g., Critical, High, Medium, Low) based on pre-defined criteria, allowing support staff to focus their efforts effectively. This prioritization could be automated based on s in the ticket description or the user’s role.
Escalation Procedures
Complex issues requiring specialized knowledge or expertise often necessitate escalation to senior support staff. Clear escalation procedures ensure a smooth handoff and prevent delays. This typically involves a defined process for forwarding the ticket to the appropriate team or individual, along with all relevant information, including initial troubleshooting steps taken and any temporary workarounds implemented. A well-defined escalation path, documented in an internal knowledge base, minimizes confusion and ensures consistent handling of complex issues. For instance, a ticket involving a database error might be escalated to the database administrator, while a security breach would be escalated to the security team.
Tracking Resolution Times and Customer Satisfaction
Monitoring ticket resolution times and customer satisfaction provides valuable insights into support performance and identifies areas for improvement. Key metrics to track include average resolution time, first response time, and customer satisfaction scores (CSAT). These metrics can be collected automatically through the ticketing system and analyzed using reporting tools. Regular review of these metrics allows for identification of bottlenecks and opportunities for process optimization. For example, consistently high resolution times might indicate a need for additional training or resources, while low CSAT scores might highlight areas where customer communication or issue resolution needs improvement. Tracking these metrics also enables the team to measure the effectiveness of implemented changes and improvements.
Proactive Support Strategies: Technical Support For Software Users

Proactive support moves beyond simply reacting to user-reported issues; it anticipates and prevents problems before they impact users. This approach significantly reduces support tickets, improves user satisfaction, and enhances overall software stability. By implementing proactive strategies, we can transform our support model from reactive firefighting to preventative maintenance.
Implementing proactive support involves identifying potential software issues before users encounter them and developing strategies to prevent common problems. This requires a multi-faceted approach combining data analysis, user feedback mechanisms, and a commitment to continuous improvement.
Identifying Potential Software Issues
Analyzing user data, such as error logs, usage patterns, and support tickets, can reveal trends and potential problems. For example, a spike in errors related to a specific feature might indicate an underlying issue requiring attention. Regularly reviewing these data sources allows for the early identification of emerging problems before they escalate into widespread user issues. This predictive analysis is crucial for preventing significant disruptions.
Strategies for Preventing Common Problems
Preventing common problems requires a proactive approach to software development and user education. This involves robust testing procedures during the development lifecycle, clear and comprehensive documentation, and the creation of easily accessible troubleshooting guides. For example, implementing automatic updates that address known vulnerabilities minimizes the risk of security breaches and related support requests. Furthermore, regular system maintenance, including database optimization and server upgrades, contributes to a more stable and reliable software experience for users.
Methods for Providing Proactive Support
Proactive support goes beyond simply preventing problems; it also involves actively reaching out to users to offer assistance and guidance. This can be achieved through various methods, including:
- Regular email newsletters: These newsletters can contain tips and tricks for optimal software usage, information about upcoming updates, and answers to frequently asked questions. For example, a newsletter might highlight best practices for data backup or explain new features in a user-friendly way.
- In-app notifications: These notifications can alert users to potential issues, such as low disk space or outdated software versions, and provide guidance on resolving them. For instance, a notification might warn a user about insufficient storage and offer solutions like deleting unnecessary files or upgrading their storage plan.
- Proactive outreach to high-value users: Identifying and supporting key users proactively can help prevent widespread issues. Regular check-ins and personalized support can build stronger relationships and improve overall satisfaction.
- Knowledge base updates and enhancements: Regularly updating the knowledge base with new information, addressing common questions, and refining existing articles ensures users have access to the most current and helpful resources.
Accessibility Considerations
Providing accessible technical support is crucial for ensuring all users, regardless of their abilities, can receive the help they need. This involves designing support systems and materials that cater to a wide range of disabilities, promoting inclusivity and equal access to information and assistance. Failing to do so creates a significant barrier to effective communication and problem-solving.
Ensuring accessible technical support requires a multifaceted approach encompassing various aspects of communication and resource design.
Inclusive Language and Communication Strategies
Using inclusive language is paramount in making technical support accessible. Avoid jargon and overly technical terms; instead, opt for clear, concise, and easily understandable language. Active listening is essential; confirm understanding by summarizing user issues and proposed solutions. Providing options for communication, such as email, phone, chat, and video calls with captioning, allows users to choose the method most comfortable for them. For visually impaired users, offering screen reader compatibility for online support materials is vital. For those with hearing impairments, providing transcripts of video tutorials and support calls is essential. Examples of inclusive language include avoiding gendered pronouns when the user’s gender is unknown (“they/them” pronouns are a good option) and using plain language instead of technical jargon. For example, instead of saying “The application encountered a null pointer exception,” one might say, “The program stopped working unexpectedly.”
Accessible Support Materials
All support materials, including documentation, FAQs, and video tutorials, must be accessible. This involves using appropriate formatting for screen readers, providing alternative text for images, ensuring sufficient color contrast, and offering transcripts for videos. Documents should be available in multiple formats (e.g., PDF, Word, HTML) to cater to various assistive technologies. For visually impaired users, high contrast color schemes, large fonts, and clear visual structure are crucial. For users with cognitive disabilities, using simple language, breaking down complex information into smaller chunks, and using clear headings and subheadings can improve understanding. For users with motor impairments, keyboard navigation should be prioritized over mouse-only interactions. Captions and transcripts are essential for videos to make them accessible to users with hearing impairments. For example, a diagram illustrating a software process should include detailed alt text describing each element and its function for screen reader users.
Support System Design
The design of the support system itself must consider accessibility. Websites and applications should be compatible with assistive technologies such as screen readers and keyboard navigation. Forms should be designed for ease of use, with clear labels and instructions. Navigation should be intuitive and predictable, allowing users to easily find the information they need. Providing multiple ways to contact support, including phone, email, and online chat, ensures accessibility for users with different communication preferences and abilities. Furthermore, real-time captioning and transcription services during live support sessions can dramatically enhance accessibility for users with hearing impairments. Regular audits of the support system’s accessibility are vital to identify and address any issues promptly. Examples of accessible design include using ARIA attributes to improve screen reader compatibility, providing clear keyboard navigation, and offering multiple input methods.
Security Best Practices in Support

Protecting user data is paramount in technical support. Robust security protocols are essential to maintain user trust and comply with data privacy regulations. Implementing strong security measures throughout the support process ensures the confidentiality, integrity, and availability of sensitive information.
Security protocols employed during support interactions must safeguard user data at every stage, from initial contact to resolution. This involves secure communication channels, data encryption, and access control mechanisms. These measures prevent unauthorized access and protect against data breaches.
Secure Communication Channels
Secure communication channels are critical for protecting user data during support interactions. All communication should be conducted over encrypted channels, such as HTTPS for web-based support or encrypted email. Avoid using unencrypted methods like plain text email or instant messaging platforms that don’t offer end-to-end encryption. The use of a VPN (Virtual Private Network) by both the support agent and the user, where appropriate, can further enhance security.
User Identity Verification
Verifying a user’s identity is a crucial step in preventing unauthorized access to sensitive information. Multi-factor authentication (MFA), requiring multiple forms of verification (e.g., password and a one-time code sent to a registered email or phone), should be implemented whenever possible. Alternatively, knowledge-based authentication, where users answer security questions about their account, can also be used. Support agents should be trained to recognize and avoid phishing attempts and social engineering tactics.
Handling Sensitive Information Securely
Handling sensitive information, such as passwords, credit card details, or personally identifiable information (PII), requires stringent security measures. All such information should be handled in accordance with relevant data privacy regulations, such as GDPR or CCPA. This includes encrypting data both in transit and at rest, using secure storage solutions, and limiting access to sensitive data only to authorized personnel. Support agents should be trained on proper data handling procedures and the importance of maintaining confidentiality. Any sensitive information shared during a support session should be documented minimally and securely, and access to such documentation should be restricted. For example, instead of writing out a full credit card number, a reference to a secure, encrypted record might suffice.
Ultimately, providing effective technical support for software users requires a holistic approach that prioritizes user understanding, efficient problem resolution, and proactive support strategies. By combining robust technical expertise with a commitment to excellent customer service, organizations can foster user satisfaction, enhance software adoption, and contribute to the overall success of their software applications. The continuous improvement of support processes, based on data analysis and user feedback, is key to maintaining a high standard of service and building strong user relationships.
